LinkedIn has recently become the center of attention due to a series of account breaches. These breaches have either led to users being temporarily locked out for safety measures or, in more severe cases, attackers taking full control of the accounts.
Cyberint’s latest report highlights a growing number of LinkedIn users voicing their grievances over the unauthorised takeovers and subsequent lockouts. What’s more alarming is the perceived inadequacy of LinkedIn’s support in addressing these concerns. Coral Tayar, a researcher at Cyberint, notes, “Despite the absence of an official statement from LinkedIn, there’s a noticeable delay in their support responses, possibly due to an inundation of help requests.”
Discussions on platforms like Reddit, Twitter, and Microsoft forums reveal users’ frustrations with LinkedIn’s purported slow or non-existent support response. One user recounted on Reddit, “Within a week, my account was compromised. I found my email altered overnight without any alert. Despite my numerous attempts, LinkedIn hasn’t addressed my concerns.”
Also Read: Cyberthreats on Social Media: The Rising Risk to Small Businesses
Furthermore, Cyberint has pointed out an intriguing pattern on Google Trends. Searches related to ‘LinkedIn account hacks’ or account recovery surged by a staggering 5,000% in recent months.
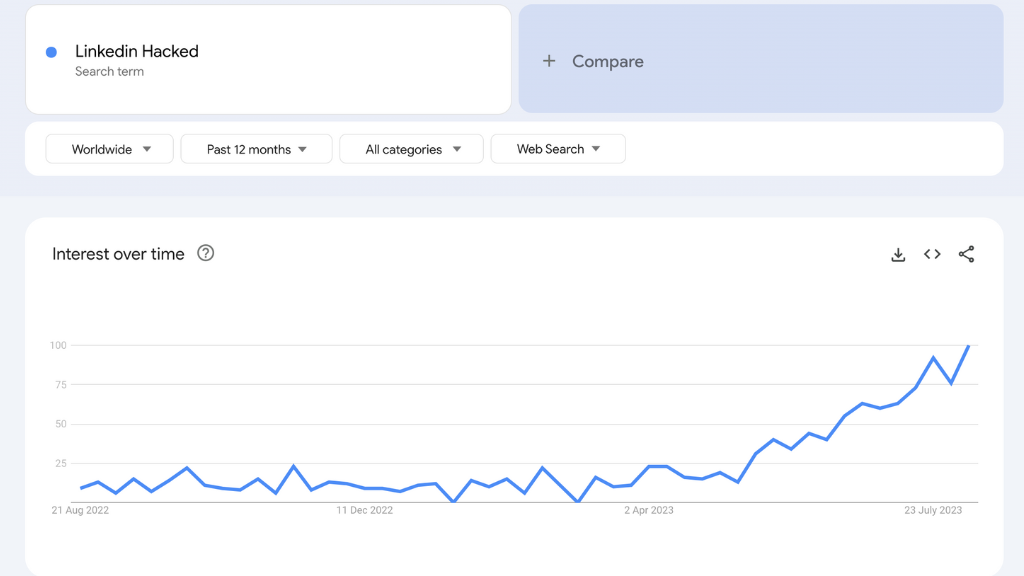
The attackers seem to employ two main methods: using previously leaked credentials or brute-force attacks, targeting a plethora of LinkedIn accounts. The platform responds by temporarily locking accounts that have strong passwords or two-factor authentication (2FA) when they detect multiple unauthorized access attempts. Subsequently, these account owners need to validate their identities and update their passwords to regain access.
Notably, when the attackers manage to breach weaker accounts, they swiftly shift the associated email to one from the “rambler.ru” domain. They then reset the password, blocking the legitimate owner’s access. Some victims also discovered that the attackers activated 2FA post-hijack, adding another layer of complexity to the recovery process.
Cyberint observed that in some instances, hackers demanded ransoms for account retrieval, while in others, they simply deleted the accounts without any demands. LinkedIn profiles are gold mines for tactics such as social engineering, phishing, and fraudulent job offers, sometimes resulting in extensive cybercrimes. Given LinkedIn’s recent efforts to counteract fake profiles and deceptive activities, hackers now find it more advantageous to seize existing accounts. For LinkedIn account holders, it’s crucial now more than ever to enhance security settings. Adopting 2FA and setting a unique, robust password is strongly recommended.






0 Comments