Chat GPT, powered by advanced natural language processing and artificial intelligence techniques, has emerged as a valuable tool in various fields. One area where Chat GPT shows great potential is cyber security.
In the digital age, where cyber threats are becoming increasingly sophisticated, leveraging AI-powered chat prompts can enhance threat detection, incident response, user education, vulnerability assessment, and many other aspects of cyber security. This article explores some examples of Chat GPT prompts for cyber security by experts and highlights their benefits and applications.
Chat GPT Prompts for Cyber Security
As advancements in artificial intelligence continue to reshape various industries, integrating AI into communication platforms, such as Chat GPT, has brought both convenience and security concerns. Here are some examples of Chat GPT prompts for cybersecurity.
Threat Detection and Analysis
One crucial aspect of cyber security is identifying and analyzing potential threats to stay one step ahead of cybercriminals. Chat GPT can comb through vast amounts of data, including logs, network traffic, and system events, to detect patterns and anomalies.
Training the model with specific prompts related to cyber security threats enables it to identify suspicious activities and potential breaches more effectively.

Examples:
- “Analyze firewall logs and identify any unauthorized or suspicious inbound connections.”
- “Monitor system processes and flag any abnormal behavior or potential malware indicators.”
- “Conduct a deep scan of the network to identify any hidden or stealthy malware infections.”
- “Analyze email headers and content to detect phishing attempts or email spoofing.”
- “Review web server logs for any unusual HTTP requests or patterns indicative of an attack.”
- “Scan database logs and identify any unauthorized access attempts or unusual data queries.”
- “Analyze DNS traffic and detect any signs of domain hijacking or DNS poisoning.”
- “Perform vulnerability scans on network devices and identify any potential weaknesses or misconfigurations.”
- “Analyze network traffic patterns to detect any large data exfiltration or unusual data transfers.”
- “Monitor system login attempts and identify any brute-force attacks or login anomalies.”
Incident Response and Handling
Effective communication and coordination among security teams are paramount during a cyber attack. Chat GPT can be a real-time assistant, helping incident response teams collaborate and share information efficiently.
Using natural language prompts, security professionals can communicate with the model to gather relevant information, receive recommended actions, and document incident details.
Examples:
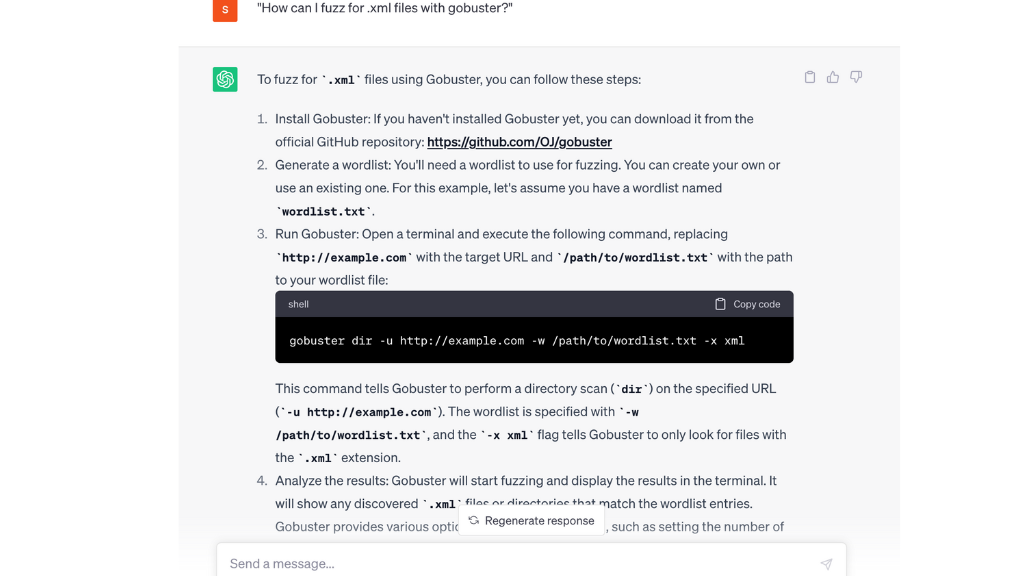
- “How can I fuzz for .xml files with gobuster?”
- “Guide the incident response team through collecting and preserving evidence from compromised systems.”
- “Assist in restoring systems from a backup to recover from a ransomware attack.”
- “Provide step-by-step instructions to mitigate the impact of a distributed denial-of-service (DDoS) attack.”
- “Assist in performing a forensic analysis on compromised systems to identify the incident’s root cause.”
- “Facilitate communication and collaboration among incident response team members during a major security incident.”
- “Recommend and execute incident containment measures to minimize further damage or data loss.”
- “Assist in generating incident response reports with detailed timelines, actions taken, and lessons learned.”
- “Guide the incident response team through notifying and engaging law enforcement agencies, if necessary.”
- “Assist in conducting post-incident reviews to identify vulnerabilities and improve incident response procedures.”
User Education and Awareness
One of the biggest challenges in cyber security is ensuring that users know the risks and how to protect themselves. Chat GPT can be an interactive chatbot to engage users and provide valuable information about cyber threats, safe online practices, and best security practices.
By adopting a conversational style, the chatbot can effectively educate users on phishing, password security, and social engineering, empowering them to make informed decisions and stay vigilant in the digital realm.
Examples:
- “Provide interactive cybersecurity training sessions to educate users on best practices for securing their home networks.”
- “Simulate phishing attacks to train employees on how to recognize and report suspicious emails or messages.”
- “Create customized security awareness campaigns targeting specific user groups within the organization.”
- “Offer tips and guidance on securing personal devices, such as smartphones and laptops, against common threats.”
- “Answer frequently asked questions about password hygiene and recommend password manager tools for better security.”
- “Provide real-time alerts and warnings to users about ongoing security threats or emerging vulnerabilities.”
- “Assist in developing and disseminating security policies and guidelines to all employees.”
- “Offer guidance on safe web browsing practices, including avoiding suspicious websites and downloading files from trusted sources.”
- “Educate users on the risks of public Wi-Fi networks and provide tips on securing their connections while traveling.”
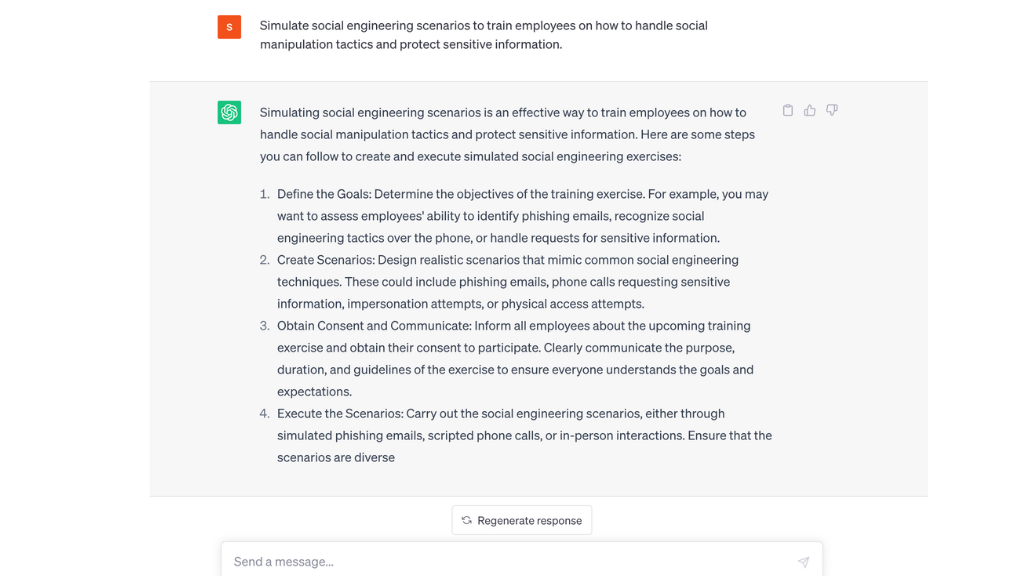
- “Simulate social engineering scenarios to train employees on how to handle social manipulation tactics and protect sensitive information.”
Vulnerability Assessment and Penetration Testing
Vulnerability assessment and penetration testing are crucial components of any robust cyber security program. Chat GPT can enhance these processes by simulating realistic chat interactions with network devices, applications, and systems.
By automating certain aspects of the assessment and testing procedures, Chat GPT can help security professionals identify vulnerabilities, test the effectiveness of defenses, and provide actionable insights to strengthen the overall security posture.
Examples:

- “How can i scan SMB with vulnerabilities with Nmap?”
- “Simulate a phishing campaign targeting employees to assess their susceptibility and raise awareness about social engineering threats.”
- “Perform a penetration test on web applications to identify potential security flaws and suggest remediation measures.”
- “Analyze wireless network configurations and recommend security enhancements to prevent unauthorized access.”
- “Review server configurations and recommend hardening measures to protect against known vulnerabilities and exploits.”
- “Assess the effectiveness of physical security controls by simulating unauthorized access attempts to restricted areas.”
- “Evaluate the resilience of network infrastructure against distributed denial-of-service (DDoS) attacks and propose mitigation strategies.”
- “Conduct a vulnerability assessment on IoT devices to identify potential entry points for attackers and recommend security measures.”
- “Assess the security posture of third-party vendors by conducting security audits and reviewing their practices.”
- “Review the organization’s incident response plan and simulate different attack scenarios to identify areas for improvement.”
Security Policy Development and Compliance
Developing and maintaining comprehensive security policies is vital for organizations to protect their assets and ensure regulatory compliance. Chat GPT can assist in this process by generating initial drafts of security policies based on established frameworks and industry best practices. Furthermore, it can help update policies as new threats emerge or regulations change. Chat GPT’s ability to analyze and interpret complex security-related information can save time and effort for security teams, allowing them to focus on implementation and enforcement.
Examples:
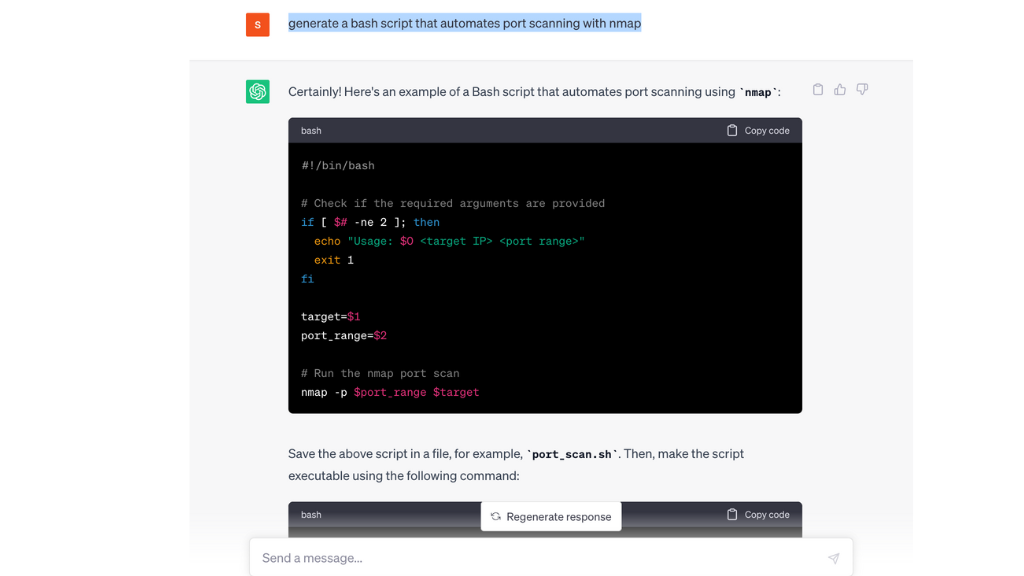
- “Generate a bash script that automates port scanning with Nmap.”
- “Provide guidance on drafting data protection and privacy policies in accordance with applicable regulations, such as GDPR or CCPA.”
- “Review existing security policies and suggest updates to align with industry best practices and evolving threat landscapes.”
- “Assist in developing a password management policy that promotes strong passwords and regular password updates.”
- “Offer recommendations for creating a mobile device management policy to secure employee devices and protect corporate data.”
- “Assist in establishing a network access control policy to ensure only authorized devices can connect to the organization’s network.”
- “Provide guidance on creating an incident response policy that outlines roles, responsibilities, and escalation procedures.”
- “Help define a patch management policy to ensure timely updates and vulnerability remediation across systems and software.”
- “Assist in developing an encryption policy to protect sensitive data at rest and in transit.”
- “Guide the creation of an employee training and awareness policy to promote a security-conscious culture within the organization.”
Chat GPT for Threat Intelligence
Threat intelligence plays a critical role in proactively defending against cyber threats. Chat GPT can collect, analyze, and summarize threat intelligence from various sources, including open-source intelligence, dark web monitoring, and security vendor feeds.
Training the model with prompts related to threat intelligence can assist in identifying emerging threats, providing contextual insights, and recommending proactive defense strategies. Chat GPT can augment security analysts’ capabilities and empower organizations to stay ahead of cybercriminals.
Examples:
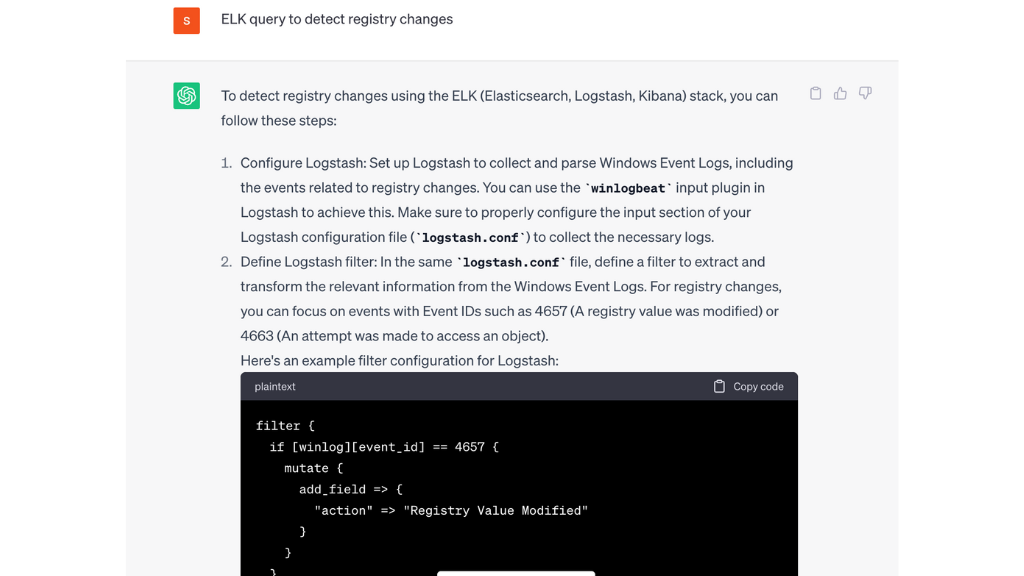
- “ELK query to detect registry changes”
- “Analyze threat intelligence feeds and generate reports on emerging malware strains and their associated indicators of compromise.”
- “Correlate and analyze security event logs to identify patterns and potential indicators of advanced persistent threats (APTs).”
- “Track and analyze social media accounts and online communities to detect chatter about potential cyber attacks or vulnerabilities.”
- “Gather information from open-source intelligence (OSINT) to assess the reputation and credibility of threat actors and hacker groups.”
- “Provide intelligence briefings on the latest tactics, techniques, and procedures (TTPs) cybercriminals use.”
- “Analyze phishing emails and extract indicators of compromise (IOCs) to contribute to the organization’s threat intelligence database.”
- “Monitor and analyze network traffic for anomalous behavior or suspicious communications that could indicate a cyber attack in progress.”
- “Conduct reconnaissance on potential targets to identify vulnerabilities and weaknesses that threat actors can exploit.”
- “Generate regular reports on the threat landscape, including emerging threats, industry-specific risks, and recommended countermeasures.”
Conclusion
Using Chat GPT prompts for cyber security has proven invaluable in combating the ever-evolving landscape of digital threats. By harnessing the power of artificial intelligence and natural language processing, these prompts provide insights, guidance, and solutions to enhance our online security measures.
However, to safeguard our digital assets and maintain a robust defense against cyberattacks, partnering with a trusted cybersecurity firm like NextDoorSec is essential.






0 Comments