In the midst of Twitter’s challenging metamorphosis towards X, subscribers of Twitter Blue are falling prey to a sophisticated phishing scam. The potential repercussions are potentially severe.
As Twitter’s owner, Elon Musk, and its newly appointed CEO, Linda Yaccarino, work towards transforming the platform into X, the path has been challenging. Rebranding endeavours at the company’s headquarters have been far from successful, and the discrepancies between the platform’s website and mobile applications are causing significant disruption for its users.
One malicious actor exploits this chaos, offering Twitter Blue subscribers the promise of seamless membership transition to X. Unfortunately, this scheme only grants the cybercriminal total access to the unsuspecting users’ Twitter accounts.
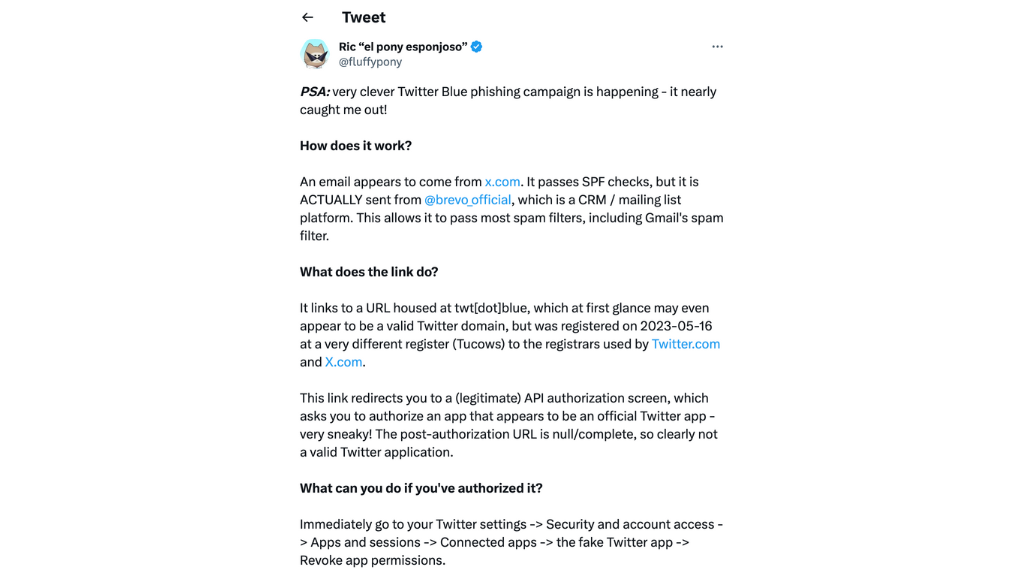
To the untrained eye, the phishing emails originate from an authentic source, displaying ‘[email protected]’ as the sender’s name. The email successfully bypasses SPF authentication checks despite originating from the mailing list platform Brevo, previously known as Sendinblue.
Also, Read Call of Duty Under Siege: How a Worm Infected Online Gaming Sessions.
A tweet from user @fluffypony reveals the email’s deceptive content, stating that the victim’s “current subscription is nearing its expiration and requires migration,” with a hyperlink guiding users to an entirely legitimate API authorisation page. This authentic interface deceives the user into granting access to their Twitter account.
This access grants the cybercriminal abilities beyond just viewing. They can modify followers, alter profile and account settings, post and delete tweets, interact with others’ tweets, and more.
The silver lining is that Twitter makes it relatively straightforward to revoke API access. This can be done by going to Settings > Security and account access > Apps and sessions > Connected apps. Regularly checking these settings is advisable, not only for those targeted by this specific phishing attack but for all users, as part of maintaining safe internet practices. As for those who fail to act quickly in turning off the untrustworthy service, the aftermath is still being determined. In the worst-case scenario, they may lose control of their accounts with unknown activities, which might necessitate the usage of identity theft protection software.






0 Comments