Hello friend,
I wanted to start with the basics of Kali Linux. But before that, I would like to show you where we are as ethical hackers in the cybersecurity realm.
Image Credits: https://www.linkedin.com/pulse/map-cybersecurity-domains-version-20-henry-jiang-ciso-cissp | I’ve recreated it & changed some things for myself.
With time, I want to cover all of the significant subdomains, but for now, I will stick to Risk Assessment.
A penetration test can be further broken down to Red & Blue teaming.
The red team is the ethical hackers in the company trying to identify & exploit the system in a stealthy way, just like in a real-world scenario.
The blue team is the company’s cybersecurity personnel, also referred to as SOC (Security Operations Centre). They’re the ones actively defending the company, by adding their human intelligence to the automated tools and technologies. They’re the people with secure application development skills.
A Purple Team is more of a concept rather than a function within the company. It may consist of senior security personnel that analyzes how the red and blue team work together and provide feedback.
As penetration testers, we need to have an understanding of all cybersecurity domains on the image above, because our task is to exploit them, by making them do things they’re not supposed to do. The more you know, the more creative you become.
As you can see, we’re just a small part of the cybersecurity industry, but in my opinion, we have the most significant impact.
To dive even deeper
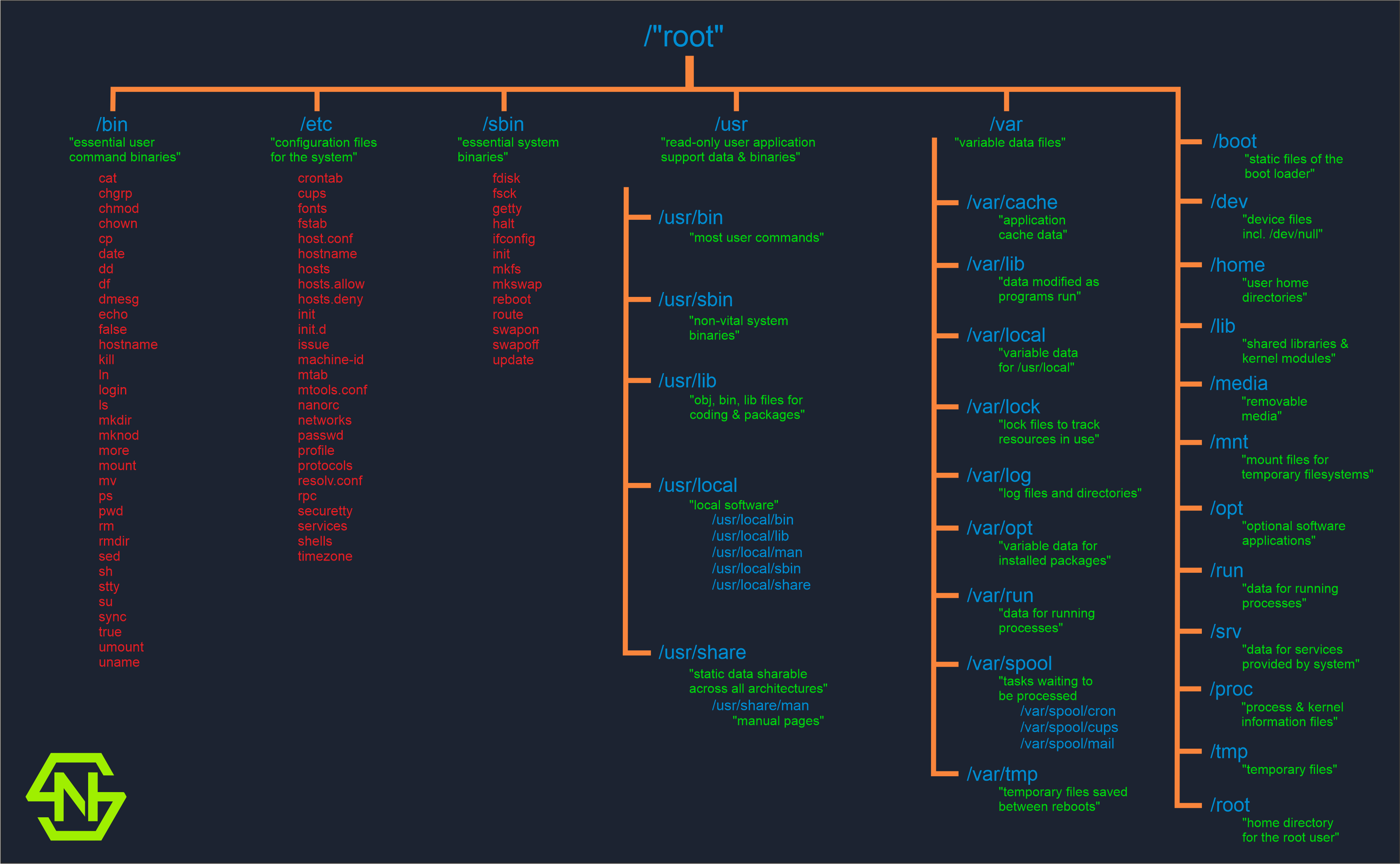
Now that we have explored the red and blue teaming concept. Let us go further into the Filesystem Hierarchy Standard (FHS) of Linux Foundation. It’s a hierarchy for file and directory placement under UNIX-like operating systems. The place where we’ll spend most of our time, therefore, it’s a good idea to get familiar with it.
In case you’re willing to know more about this FHS, here’s the link to the source of my infographic’s data with further details.







0 Comments
Trackbacks/Pingbacks