Regarding protecting your computer network from cyber threats, firewalls, and IDS (Intrusion Detection Systems), IPS are three of the most common technologies. While they have the same general objective of protecting computer systems and networks, there are significant differences.
Here, we will explore the differences between firewalls and IDS, IPS, and how they work to safeguard against cyber threats.
Difference Between Firewall and IDS, IPS
In today’s interconnected world, cyber-attacks are a real and present danger. A single breach in a system can cause significant damage, both financially and reputationally. Cybersecurity measures have become essential for any organization or individual using computer systems. The most commonly used steps are firewalls, intrusion detection systems, and Intrusion prevention systems.
What is a Firewall?

It is a network security device that watches and screens incoming and outgoing web traffic. Its primary purpose is to block unauthorized access while permitting authorized communications. It does this by analyzing network packet source and destination addresses and comparing them to a set of rules.
Also See: Nmap Review: The Ultimate Network Scanning Tool for IT Professionals in 2023
How Does a Firewall Work?
A firewall works by examining each packet of data entering or leaving the network and comparing it to predefined rules. If the packet matches the rule, it can pass through; if it doesn’t, it is blocked. Firewalls can also be configured to log the blocked packets, allowing administrators to identify and address potential threats.
Strengths
Firewalls have several strengths, including:
- Effective in blocking known threats.
- They can be configured to block specific types of traffic, such as peer-to-peer file sharing or instant messaging.
- Easy to implement and manage.
- They can be used to enforce company security policies.
Limitations
Despite their effectiveness, firewalls have certain limitations, including:
- Cannot detect new or unknown threats.
- Can be bypassed by sophisticated attacks that exploit vulnerabilities in the network or the firewall itself.
- They do not provide detailed information on the type or source of the threat.
What is an IDS?
An intrusion detection system (IDS) is a tool or software application that watches a network or system for malicious activity or policy violations. It identifies potential security breaches by analyzing system activity and detecting unusual patterns or anomalies.
How does an IDS Work?
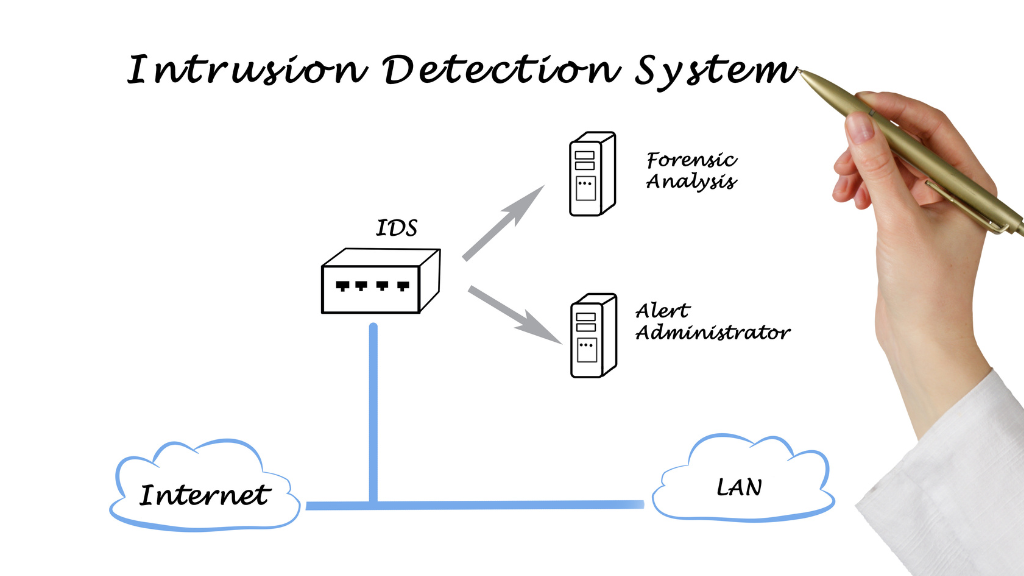
An IDS analyzes the network traffic and looks for patterns that indicate a potential attack. It can also monitor system logs and audit trails for suspicious activities. When it notices a possible danger, it warns the administrator, who can take appropriate action to prevent the attack.
Strengths
IDS has several strengths, including:
- Detect both known and unknown threats.
- Provide more detailed information on the type and source of the attack.
- Configured to monitor specific types of traffic or applications.
- Used to detect insider threats or policy violations.
Limitations
Despite its strengths, IDS also has certain limitations, including:
- Generate false positives, leading to unnecessary alerts and additional administrative workload.
- Can be resource-intensive, requiring constant monitoring and analysis of network traffic.
- May not be effective against sophisticated attacks that use encryption or other advanced techniques to evade detection.
What is an IPS?
Intrusion Prevention System or IPS, is a security system that detects and prevents potential cyber threats by analyzing network traffic. It operates at the network layer and can be hardware or software-based, and its primary purpose is to identify and block malicious traffic before it can cause harm to the network or system.
How Does an IPS Work?
An IPS analyzes network traffic in real-time using various techniques such as signature-based detection, behavioral analysis, and anomaly detection. It identifies potential threats and can take actions such as blocking traffic, alerting system administrators, or terminating the connection.
An IPS can also learn from experience to improve its detection accuracy and reduce false positives.
Strengths
- Real-time protection against various types of cyber threats
- Comprehensive protection for the network or system
- Automatic response to potential threats
- Learning ability to improve detection accuracy and reduce false positives
Limitations
- High cost to implement and maintain
- Potential for generating false positives
- Impact on network performance due to traffic analysis
Firewall Vs. IDS Vs. IPS
Function
The basic role of a firewall is to monitor and control traffic based on predefined security rules. On the other hand, an IDS is designed to detect and alert you of potential threats in real-time, and an IPS not only detects threats but takes action to prevent them.
Placement
A firewall is placed at the network perimeter, an IDS is placed on the internal network, and an IPS can be placed in either location.
Traffic Filtering
A firewall filters traffic based on predefined rules, while an IDS and IPS can analyze traffic behavior and take action accordingly.
Attack Prevention

A firewall cannot prevent attacks, while an IDS can detect them in real time and alert you. An
IPS goes beyond detection and takes action to prevent them. It can block traffic, modify it, or even alert the system administrator to take the necessary steps.
Performance Impact
Firewalls have a minimal impact on network performance, while IDS and IPS systems can significantly impact depending on their complexity.
Deployment
A firewall is relatively easy to deploy and manage, while IDS and IPS systems require more effort and expertise to deploy and maintain.
An IPS in a firewall complements its capabilities, providing additional protection against cyber threats.
Conclusion
Understanding the differences between the firewall and IDS/IPS is crucial for implementing a strong network security strategy. While firewalls act as a barrier to block unauthorized access to a network, IDS/IPS provide deeper inspection and detection of potential security threats by monitoring network activity.
Partnering with a reputable cybersecurity firm such as NextDoorSec is recommended for organizations looking to enhance their cybersecurity posture.






0 Comments