With the rise of online surveillance and censorship, people are turning to alternative means of accessing the internet. Tor is a solution that provides users with a private and secure online experience, and Tor browser online also allows users to access censored or blocked websites in their country.
One of the most popular use is to download from Tor anonymously. In this article, we’ll explore the world of downloading from Tor and provide tips and best practices to help you do it safely and securely.
What is Tor, and How does it work?
The Onion Router, or Tor, is an open-source, free program that lets individuals access the web secretly. It functions by encoding the data you send over the internet and channeling it via several routers or nodes, rendering it challenging for anybody to track your online activity to you.
Tor routes your web traffic across a network of secure proxies, making it impossible for anybody to monitor your online activity. When you use the web browser Tor to download and do other activities, it encrypts your internet traffic and sent to a Tor relay, which then sends it to another relay, and so on, until it gets its final destination.
Nobody can easily track the traffic back to its origin since every link only knows the IP addresses of the ones that come before and after it in the sequence. This also means that the website you’re visiting doesn’t know your IP address but instead sees the IP address of the last relay in the chain.
Also See: Tips for Secure Downloading with VPN
Downloading Tor dl

You can download the Tor Browser for PC Windows,7, 10, and other versions of Windows directly from the Tor Project’s website. It is also available for other operating systems, such as macOS and Linux.
The Tor Project also provides a version of the Tor Browser for Android devices. It works similarly to the desktop version, allowing you to access the Tor browser installer and browse the web anonymously.
The Tor Browser is available for iOS devices, but it’s important to note that it’s not as secure as the desktop or Android versions due to the restrictions Apple places on apps in the App Store. The iOS version of the Tor Browser is based on a modified version of Firefox and is only available through the App Store.
You can use the Tor Browser to visit the dark web. The dark web includes parts of the internet not indexed by traditional search engines and can only be accessed through specific software such as the Tor Browser. However, caution is essential when browsing the dark web, as potential risks and illegal content are present.
Go to the Tor Project’s website and click the “Download Tor” button. You’ll be directed to a page with different versions of Tor for other operating systems.
On Windows
- Download the Tor Browser for Windows from the Tor Project’s website.
- Once you complete the download, double-click the file to begin the installation.
- Choose the language you want to use and click “OK.”
- Click “Install” to start the installation process.
- Once the installation is complete, tap “Finish” to launch the Tor Browser.
For Mac OS
- Download the Tor Browser for Mac OS from the Tor Project’s website.
- Once the download is complete, drag the Tor Browser icon to the Applications folder.
- Launch the Tor Browser by double-clicking on the Tor Browser icon in the Applications folder.
On Linux
- Run the Terminal application on the Linux system.
- Add the Tor Project’s package signing key to your system by running a command:
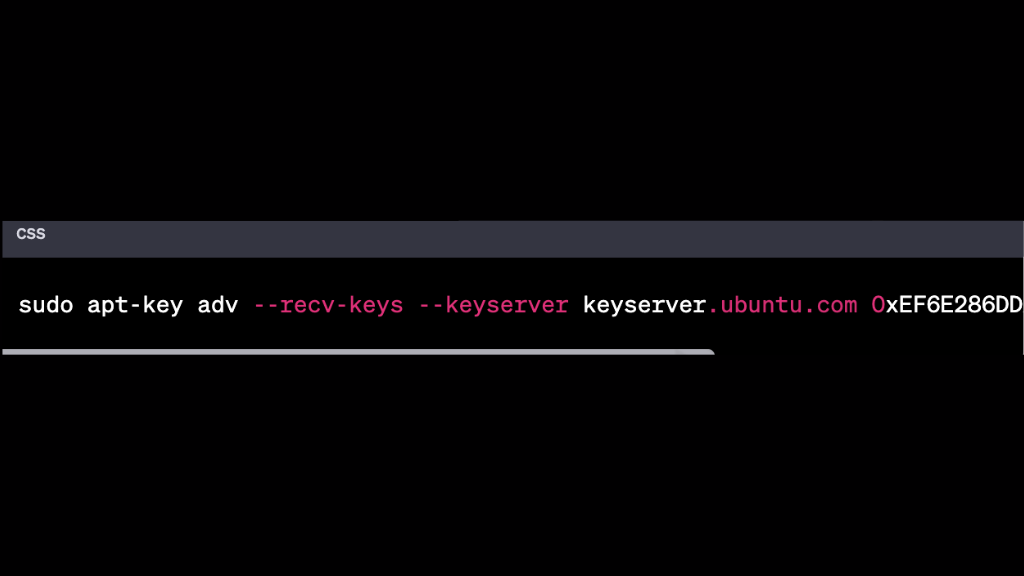
Add the Tor Project’s repository to your system by running the following command:
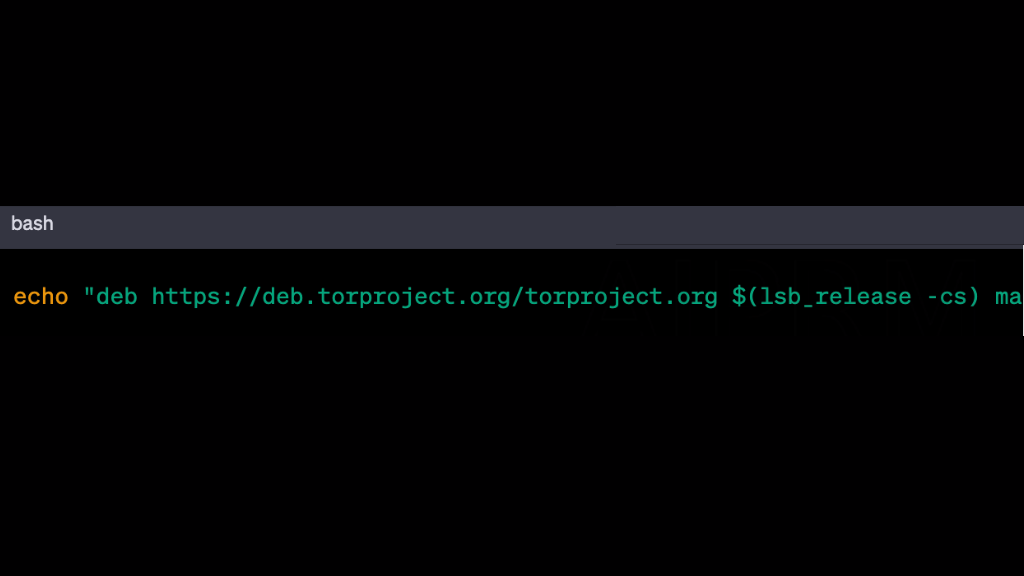
Update your package list by running the following command:
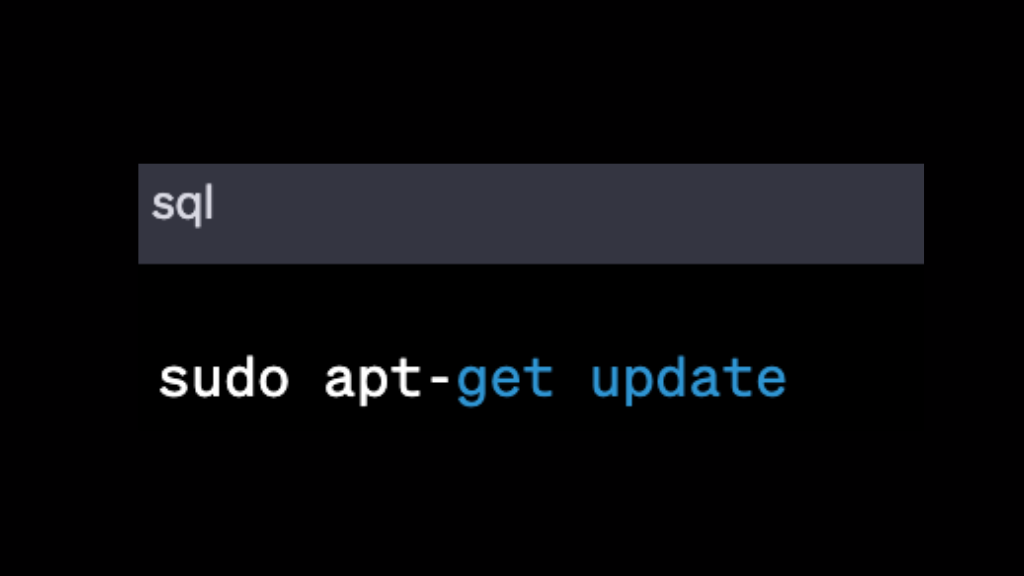
Install the Tor Browser by running the following command:
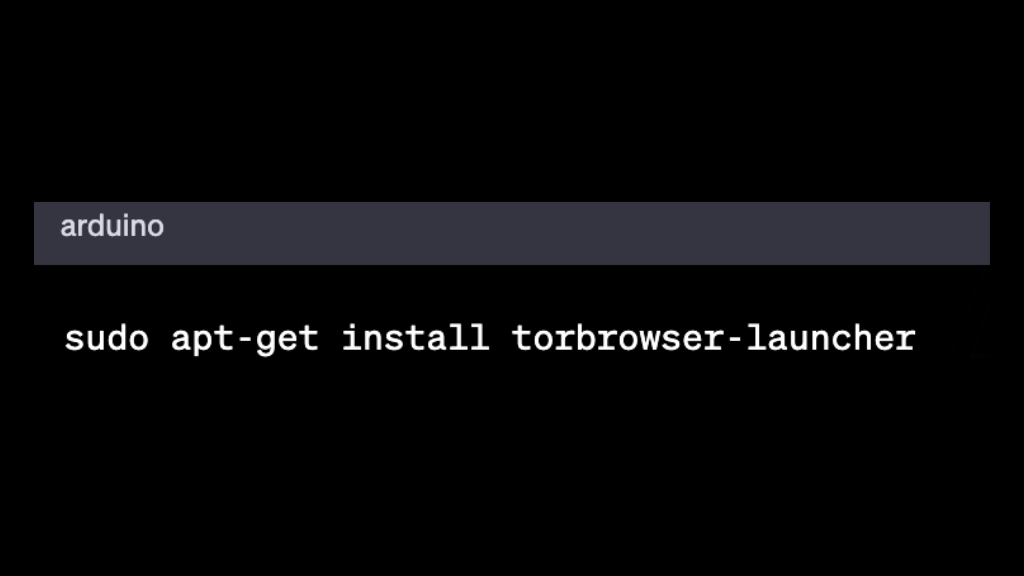
Launch the Tor Browser by searching for it in your application menu.
Using Tor
To use Tor, launch the Tor Browser and browse the web. The Tor Browser is based on Mozilla Firefox and has built-in privacy features such as NoScript and HTTPS Everywhere.
When you use Tor, it’s essential to remember that it can slow down your internet connection, and some websites may not work correctly.
Is Downloading From Tor Safe?
While Tor is an excellent online privacy and security tool, downloading from Tor can be risky. Cybercriminals often use the Tor network to distribute malware, illegal content, and other malicious files.
This is because Tor makes it difficult for law enforcement agencies to track the origin of illegal activities.
Is it Legal to use Tor?
Yes, using Tor is legal in most countries. However, people use Tor for illegal activities such as drug trafficking, hacking, and child pornography. It’s important to note that while Tor can provide anonymity, it doesn’t make you invincible.
Law enforcement agencies and other third parties can still track your online activities through other means, such as analyzing your internet traffic.
Can the FBI track Tor?
The FBI has been known to use various techniques to track users on the Tor network, including exploiting vulnerabilities in the Tor Browser or targeting individuals who have misconfigured their Tor software. Additionally, law enforcement agencies may use traffic analysis or other sophisticated methods to identify Tor users.
That being said, it’s important to note that the FBI would need a valid legal reason to track someone on the Tor network, such as a court order or warrant. Using Tor is not a crime, and users who use the web for legal purposes are generally not at risk of being tracked or prosecuted by law enforcement agencies.
Conclusion
When you download from Tor, it provides you with a high degree of privacy and security, especially when accessing content that may be blocked or censored in your country. However, it’s essential to use caution when downloading files from Tor and to follow best practices for online security to minimize the risk of malware or other security threats.
If you seek expert guidance on staying safe and secure online, consider contacting Nextdoorsec. This leading cybersecurity firm specializes in providing tailored solutions to help individuals and businesses protect their digital assets.






0 Comments