In today’s digital age, where online anonymity and accessibility have become paramount, understanding “how do residential proxies work” is vital. Whether you’re a business looking to gather unbiased data, a privacy advocate seeking online anonymity, or a techie curious about modern internet mechanics, this article is your comprehensive guide. With our expertise on this topic, we promise to give you an engaging, detailed, and concise exploration of the workings of residential proxies.
What are Residential Proxies?
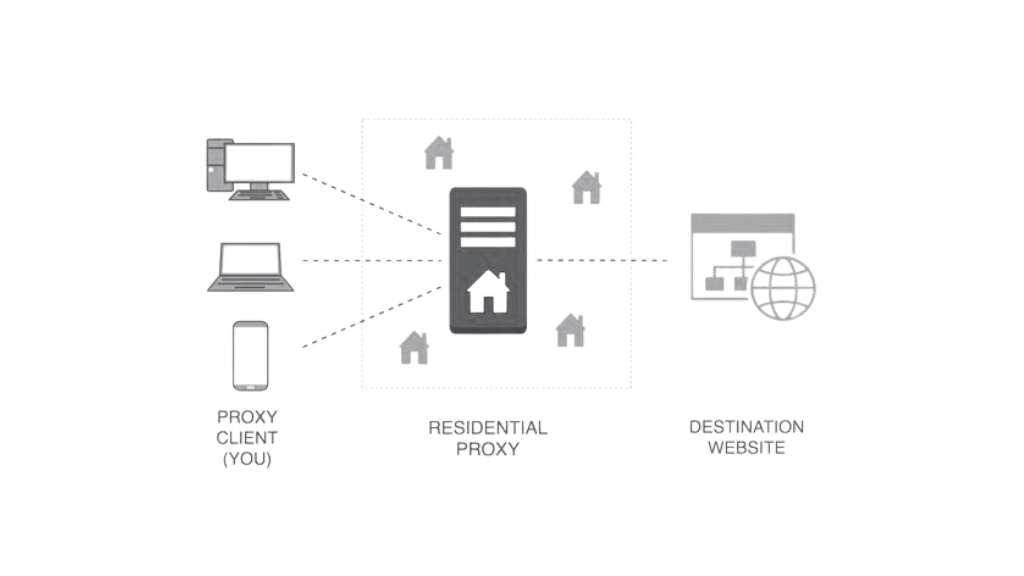
A residential proxy is a type of intermediary server that uses an IP address provided by an Internet Service Provider (ISP). Unlike other types of proxies that originate from data centers, residential proxies hail from actual devices and homes, making them look more legitimate on websites and online platforms.
What Makes Residential Proxies Unique?
- Authentic IP Addresses: The IPs tied to these proxies originate from real internet service providers, making them difficult to identify and block.
- High Anonymity Level: Given their residential nature, they are less likely to flag or blacklist them, ensuring smoother online interactions.
- Dynamic Rotation: Some residential proxies offer rotating features, changing the IP address periodically enhancing online security.
How Do Residential Proxies Work?
Delving deeper into the mechanism of these proxies illuminates their efficiency and distinctiveness.
- The Mechanism Behind Residential Proxies: When using a residential proxy, your request passes through a residential IP address – essentially an IP that belongs to an actual device in someone’s home.
- Differentiating Between Residential and Data Center Proxies: While both mask your original IP, residential proxies use legitimate IP addresses from ISPs. In contrast, secondary corporations provide data center proxies, which websites flag more easily.
Benefits of Using Residential Proxies
Understanding the perks of these proxies can aid in making informed decisions for online activities.
- Enhanced Privacy and Anonymity: With residential IPs, your online actions mirror that of a regular user, providing superior privacy.
- Reduced Chances of Being Blocked: Many sites detect data center proxies and block them, but they often overlook residential proxies because they look genuine.
Applications of Residential Proxies
These proxies aren’t just for anonymity; they have varied applications enhancing different online experiences.
- Web Scraping and Data Extraction: They gather data efficiently without getting blocked.
- Accessing Geo-restricted Content: Bypass regional restrictions and access global content seamlessly.
- Sneaker and Retail Copping: Secure limited edition items online by mimicking multiple genuine users.
Downsides of Using Residential Proxies
No tool is without its cons, and residential proxies are no exception.
- Potential for Misuse: Malicious users can exploit these proxies for nefarious activities, casting a shadow over their genuine users.
- Cost Implications: Quality residential proxies can be pricier than their data center counterparts due to their advantages.
Selecting the Right Residential Proxy Provider
With a multitude of providers, how does one choose?
- Important Factors to Consider: Look into their pool size, rotation settings, and customer reviews.
- Recommendations and Reviews: Always do your homework by researching and reading user reviews.
Also See: Experts’ Tips on How to Use Proxies in Chrome for Optimal Performance
Rotating Proxies: A Game-Changer
Enter the world of rotating residential proxies. Instead of using a single IP address, these proxies rotate among a pool of IP addresses, making it harder for websites to detect and block them. Whether it’s a “proxy rotating” or “proxies rotating,” the concept remains the same. They enhance security, provide anonymity, and reduce the risk of blacklisting.
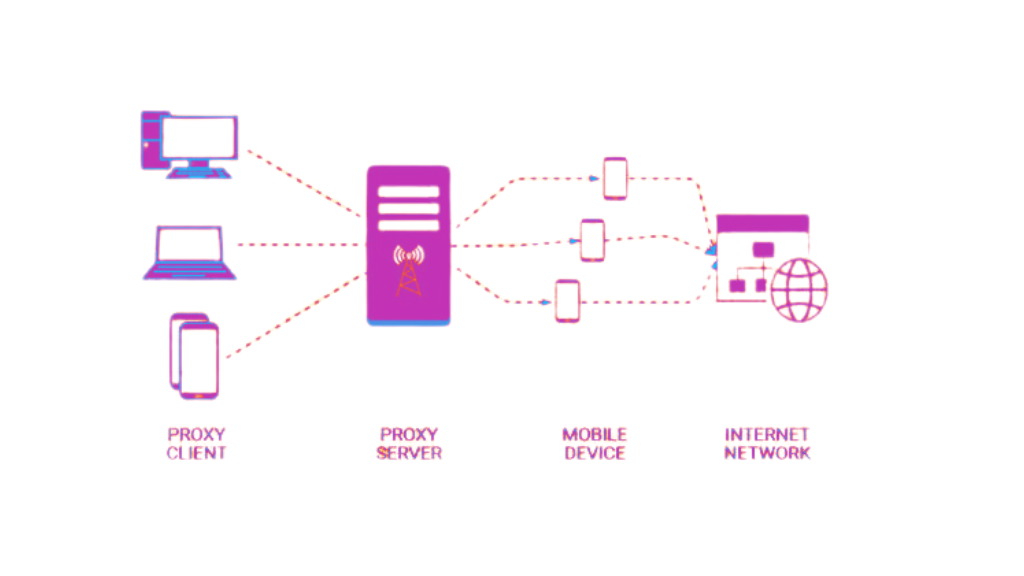
The Allure of Mobile Residential Proxies
Mobile residential proxies provide an IP address from a mobile device. Given the surge in mobile internet usage, tapping into mobile residential proxies allows users to emulate genuine mobile traffic, proving invaluable for tasks like mobile ad verification or market research.
Residential Proxy vs. VPN
A common debate in online circles is “residential proxy vs. VPN.” Both tools offer online anonymity, but they function differently. While a VPN routes your entire device’s traffic through another server, a residential proxy works at the application level, affecting only specific programs or browsers. This granularity makes residential proxies ideal for specialized tasks.
The Economics of Proxies
For users and businesses that recognize the benefits, there’s often a quest to find rotating residential proxies cheap. However, as with all things, you get what you pay for. It’s essential to strike a balance between affordability and reliability.
Purchasing Residential Proxies
When you’re ready to dive in, there are ample opportunities for residential proxies buy options online. From dedicated providers to marketplaces, sourcing residential proxies online has never been easier. However, it’s crucial to do thorough research, read reviews, and ensure you’re getting genuine residential IP addresses.
Conclusion
By understanding the intricacies of how residential proxies operate, you can better harness their power for your online activities, ensuring both security and accessibility. Whether you choose to buy residential proxies or opt for a VPN, being informed is the key.
As online safety becomes a growing concern, ensuring that your digital activities remain untraceable and secure is paramount. If you’re keen on taking your cybersecurity to the next level, considering expert services like those offered by Nextdoorsec is a wise choice.
FAQs
1. How does a residential proxy work?
A residential proxy provides users with IP addresses from real, physical locations, making it appear as though their online actions originate from a local resident’s device.
2. Are residential proxies legal?
Yes, residential proxies are legal to use. However, how and where you use them can determine the legality. For instance, using them to bypass geo-restrictions or for illicit activities can be considered unlawful.
3. Can my IP be tracked if I use a proxy?
While proxies provide an additional layer of anonymity, they don’t make you entirely invisible. Skilled entities can potentially trace back to the original IP with the right tools and techniques.
4. Can residential proxies be traced?
Yes, like other proxies, residential proxies can be traced, especially if the proxy provider keeps logs. However, tracing might be more challenging compared to data center proxies because residential IPs come from genuine devices.
5. How do residential proxies work with IP addresses?
Residential proxies work by routing your online requests through an intermediary server that assigns you a genuine IP address from a residential location. This makes it appear as if you’re browsing from a real home device.
6. How do you get residential proxies?
To get residential proxies, one can approach proxy providers who offer them as a service. After subscribing, you’ll be given access to their pool of residential IPs to use as intermediaries for your online activities.






0 Comments