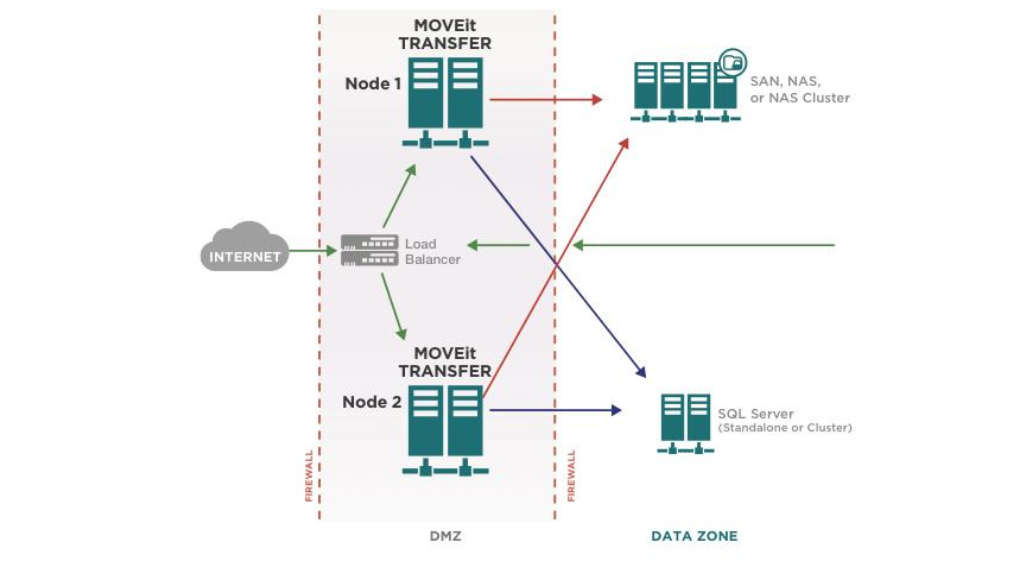
Progress Software revealed a new security MOVEit Transfer app flaw, marking the third flaw discovered. The Cl0p cybercrime gang has exploited this vulnerability to extort affected companies.
This newly identified flaw, currently lacking a CVE identifier, involves an SQL injection vulnerability. Exploiting this vulnerability could result in elevated privileges and unauthorized access to the system.
To protect their environments until a fix is available, Progress Software advises customers to turn off all HTTP and HTTPs traffic on ports 80 and 443 for MOVEit Transfer. The company is actively working on a patch to address this weakness. The cloud-managed file transfer solution has already been fully patched.
This disclosure follows Progress Software’s previous announcement of SQL injection vulnerabilities (CVE-2023-35036). These vulnerabilities could be leveraged to access the database content of the affected application.
The newly discovered vulnerabilities are in addition to CVE-2023-34362, which the Clop ransomware gang exploited as a zero-day in data theft attacks. Kroll, a security firm, reported that evidence indicates the Clop gang, also known as Lace Tempest by Microsoft, had been testing this exploit since July 2021.
Read Also: “BatCloak Engine: Cybercriminals’ Undetectable Malware”
Coinciding with this development, the Cl0p actors published a list on their darknet leak portal, revealing 27 hacked companies that they claim were compromised using the MOVEit Transfer vulnerability. Among the victims are multiple U.S. federal agencies, including the Department of Energy, as reported by CNN.
“The number of potentially breached organizations so far is significantly higher than the initial count mentioned in Clop’s previous MFT exploitation campaign involving the Fortra GoAnywhere MFT,” stated ReliaQuest.
According to Censys, a web-based search platform, approximately 31% of the exposed hosts running MOVEit belong to the financial services industry. Healthcare constitutes around 16%, information technology around 9%, and government and military sectors around 8%. The majority of these servers, approximately 80%, are located in the United States.
Based on Kaspersky’s analysis of 97 families of malware spread via the malware-as-a-service (MaaS) business model between 2015 and 2022, ransomware holds the largest share at 58%. Information stealers follow at 24%, while botnets, loaders, and backdoors account for 18% of the distribution.
According to the Russian cybersecurity company, “Money is the root of all evil, including cybercrime.” Kaspersky also highlighted how MaaS schemes enable less technically skilled attackers to participate, thereby reducing the entry barrier for carrying out such attacks.






0 Comments