In the age of digitization, online security has become paramount. Two terms that often come up in the context of cybersecurity are pharming and phishing. Although these terms are sometimes used interchangeably, they refer to different types of cyber-attacks.
The following article will shed light on “Pharming vs phishing,” providing a detailed analysis of these online threats, their similarities, differences, examples, and measures to avoid falling prey to these tactics.
Pharming vs Phishing: An Overview
Pharming
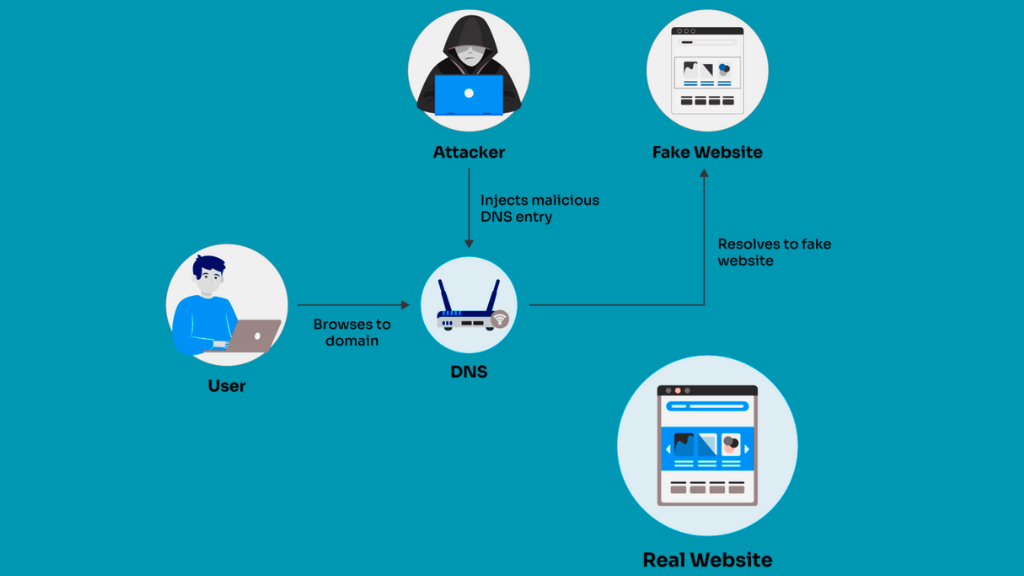
It is a cyberattack that redirects a website’s traffic to another fraudulent site without the user’s consent. The attackers usually do this to gather personal information.
Pharming in cyber security has evolved into a serious concern. This attack bypasses all user-driven actions, making it more sophisticated and difficult to detect.
A pharming attack can be detrimental as it can lead to the theft of personal information like bank account details. Since the victim is unaware that he is redirecting to a false site, they may inadvertently provide sensitive data.
Also Read: An Expert Guide on How to Prevent Keylogging in 2023
Phishing
What is a Phishing Attack? Phishing attacks are deceptive emails or messages that trick users into revealing personal or financial information. Unlike pharming, phishing relies on user interaction and often masquerades as a trustworthy entity.
Three Typical Features of a Phishing Email
Urgent Request: Phishing emails often create a sense of urgency, urging the recipient to act quickly.
Spelling and Grammar Errors: These emails may contain poor grammar and spelling mistakes.
Mismatched URLs: The link text may appear legitimate, but hovering over it reveals a different URL, leading to a malicious site.
Phishing and Phisher
The meaning of phishing revolves around the act of tricking individuals into divulging personal information. The term “phisher” refers to the attacker who carries out this deceptive practice.
Similarities Between Phishing and Pharming
Though different in their execution, phishing and pharming share some common goals and characteristics:
- Goal to Deceive: Both aim to deceive users to gather personal information.
- Involvement in Fraud: Both involve fraudulent activities and identity theft.
- Challenges in Detection: Both attacks are complex and can be challenging to detect without proper security measures.
Difference Between Phishing and Pharming
While both phishing and pharming are cyber threats aiming to steal personal information, their methods of execution are distinct.
User Interaction
- Phishing: Requires user interaction, such as clicking on a deceptive link.
- Pharming: Does not necessarily need user interaction. A user can redirect to a fraudulent website even if they typed the correct URL.
Attack Vector
- Phishing: Typically utilizes deceptive emails or messages to trick users.
- Pharming: Exploits vulnerabilities in the DNS system to redirect users to fraudulent sites.
Detection

- Phishing: Often detected by examining the content of the message or the email for suspicious links or requests.
- Pharming: Detection can be more challenging, as it requires tools to verify the legitimacy of the website’s domain.
Phishing and Pharming Examples
Real-Life Phishing Incident
Remember the high-profile incident where numerous celebrities were tricked into revealing their passwords through a well-crafted phishing email? This goes to show that anyone can fall victim if they aren’t vigilant.
Notorious Pharming Attack
There have been instances where popular e-commerce sites’ traffic was redirected to clone sites, leading to thousands of people inadvertently providing credit card details.
Pharming’s Menacing Rise
Pharming’s stealthy nature makes it a rising concern. Since users can land on a fraudulent site even when they type the correct URL, it’s like a wolf in sheep’s clothing.
Why is Pharming Effective?
The sheer sneakiness of it! Imagine entering your home, only to realize it’s an exact replica and the real one’s been moved without your knowledge. That’s pharming for you in the digital realm.
Protecting Yourself in the Digital Jungle
In this digital age, one must be vigilant. But how can one guard against such insidious threats?
Tips to Combat Phishing
- Verify the Source: If an email or message seems suspicious, it probably is. Verify before clicking.
- Update Regularly: Ensure your software is updated. Many updates contain security patches.
- Educate and Train: Awareness is the key. Regularly train staff and family on the dangers of phishing.
Measures Against Pharming

- Use HTTPS: Always check for ‘https’ in the URL. It ensures the site is encrypted.
- Update DNS Settings: Regularly update and secure DNS settings to guard against redirection.
- Install Security Software: Many security software suites now come with protection against pharming.
Conclusion
Both pharming and phishing are malicious techniques designed to deceive users and obtain sensitive information, often for financial gain. Phishing typically involves the use of fraudulent emails and websites that mimic legitimate ones, hoping to lure users into providing personal information. Pharming, on the other hand, doesn’t rely on luring users. Instead, it manipulates the DNS system to redirect users to fake websites without their knowledge. Both these cyberattacks emphasize the increasing sophistication and persistence of cybercriminals, underlining the importance of staying vigilant and informed about the ever-evolving landscape of online threats.
With the digital age seeing a rampant increase in such threats, individuals and businesses alike need to arm themselves with reliable defense mechanisms. Turning to cybersecurity experts, such as Nextdoorsec, ensures that you’re a step ahead of these malicious entities.
FAQs
1. What is an example of pharming?
Pharming is when a user is redirected from a legitimate website to a fake one due to tampered DNS settings. For instance, you might end up on a counterfeit bank site and unknowingly give away your login details.
2. What are phishing and pharming examples of?
Phishing and pharming are both examples of online fraud. Phishing often involves fake emails or messages prompting users to provide sensitive data, while pharming redirects users to a fraudulent website even if they type the correct address.
There’s a repetition in your question; “phishing” is mentioned twice. Phishing involves luring victims via fake emails or messages to steal their personal information.
3. What is phishing vs pharming vs vishing?
- Phishing: Deceptive emails or messages aiming to steal personal information.
- Pharming: Redirecting users from legitimate websites to fake ones using DNS manipulation.
- Vishing: Scam phone calls tricking people into sharing personal data or money.
4. What is a pharming attack?
A pharming attack redirects users from a genuine website to a fraudulent one by manipulating DNS settings, aiming to capture sensitive data without the user’s knowledge.
5. How is pharming similar to phishing?
Both pharming and phishing aim to deceive users and obtain sensitive information by presenting fraudulent content as legitimate.
6. What is the difference between phishing and pharming?
Phishing typically uses deceptive communications, like emails, to lure users to fake websites, while pharming redirects users to fraudulent sites by manipulating DNS entries or infecting a user’s computer.
7. What is pharming in computer?
Pharming is a cyber attack intending to redirect a website’s traffic to another, fake website without the user’s knowledge, often to steal sensitive information.






0 Comments