In today’s digital age, the security of applications is more crucial than ever. With a multitude of threats lurking in the cyber world, developers need robust tools and methodologies to protect their applications. Enter SAST vs. DAST vs. IAST – three pivotal approaches to application security. But what do these acronyms stand for, and how do they compare to each other? Let’s dive deep into this captivating realm of cyber fortification.
Understanding SAST
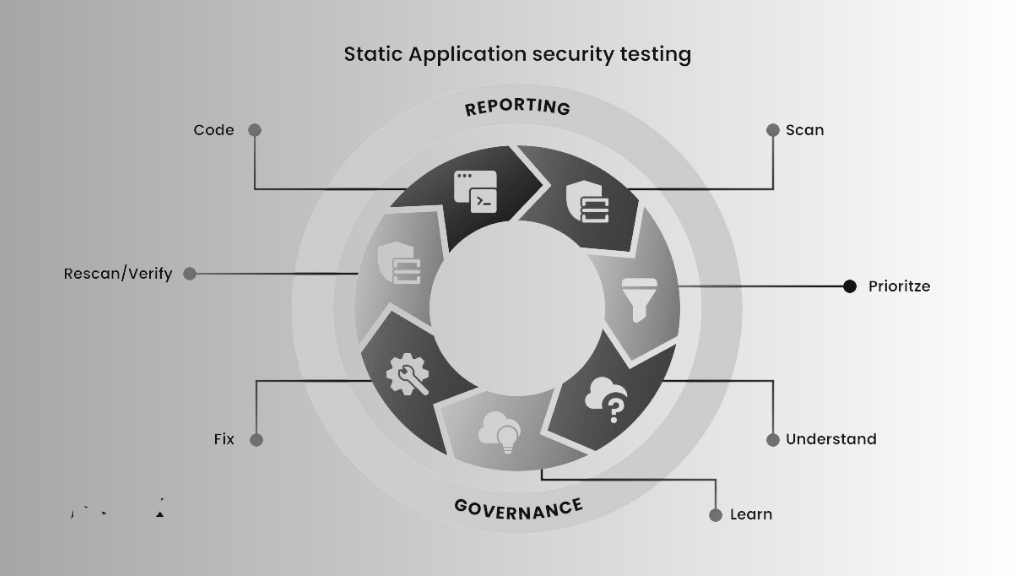
SAST stands for Static Application Security Testing. It can be likened to proofreading a book before its publication. It examines the source code, bytecode, or even binary code of applications without executing the program. This “white-box” approach delves deep into the codebase, identifying vulnerabilities before the application runs.
Core Advantages of SAST
- Early Detection: SAST pinpoints vulnerabilities during the initial development phase, saving potential future costs.
- In-depth Analysis: It provides a comprehensive view of the application, uncovering even deeply embedded flaws.
- Efficiency: With automation capabilities, it can quickly scan large codebases.
Limitations of SAST
- False Positives: Can occasionally flag non-issues.
- Scope: Unable to detect runtime vulnerabilities or issues stemming from the external environment.
Ideally, it’s best to deploy SAST during the early development stages. Why? Because catching vulnerabilities early can save time and money!
Best SAST Tools
Several SAST tools are available in the market, each with its unique features and capabilities. Some of the best SAST tools include:
- Checkmarx
- Fortify
- Veracode
- GitLab
- Coverty
- SonarQube
- Snyk
- Codacy
- Klocwork
- Semgrep
Dive into DAST

DAST stands for Dynamic Application Security Testing, which contrasts with SAST in its approach. Think of DAST as reviewing a play while it’s being performed. This “black-box” method evaluates applications during their runtime, identifying vulnerabilities that manifest only when the software is in operation.
Prime Benefits of DAST
- Runtime Analysis: Detects vulnerabilities that emerge during application execution.
- Environment Assessment: Evaluates external factors that might pose threats.
- No Source Code Needed: Can be employed even without access to the application’s internal workings.
DAST: The Drawbacks
- Late Detection: Pinpoints vulnerabilities later in the development cycle.
- Surface Analysis: Might miss vulnerabilities embedded deep within the application.
DAST shines post-development, especially when you need to test real-world scenarios.
Best DAST Tools
When it comes to dynamic application security testing, various tools stand out due to their efficiency and accuracy. The best DAST tools include:
- Indusface Pvt Ltd
- Security AppScan
- OWASP ZAP
- Detectify
- Burp Suite
- Appknox
- Metasploit
- Netsparker
- Nessus
- Nikto
DAST tools are implemented in a live environment, often in the final stages of the development cycle, to mimic potential external threats and attacks. They play a pivotal role in ensuring the real-world security of applications.
Grasping IAST
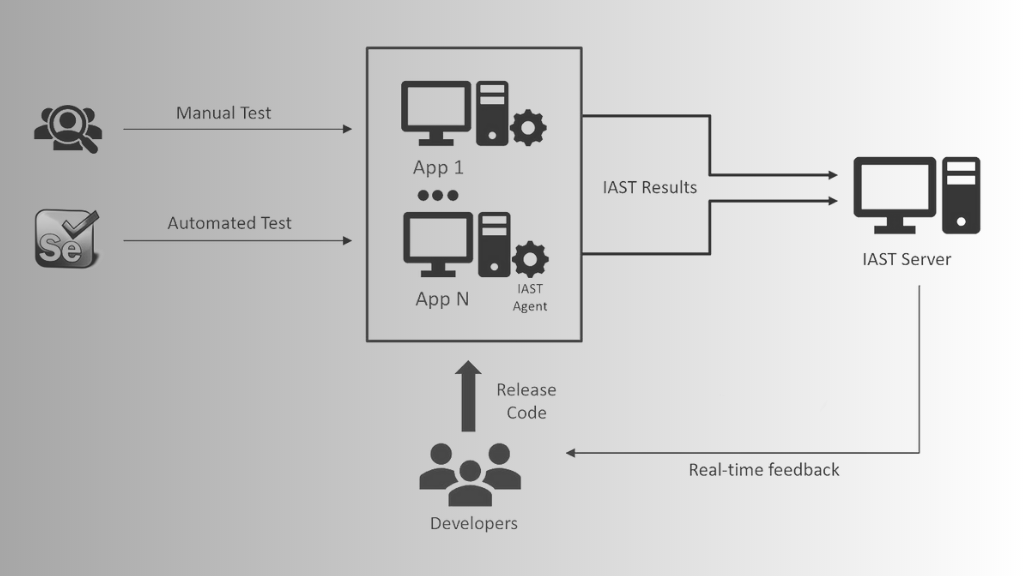
Interactive Application Security Testing (IAST) merges the best of both SAST and DAST. Imagine a critique that amalgamates pre-publication proofreading with a live performance review. IAST evaluates applications from within, using agents to monitor the application’s behavior during runtime and identify vulnerabilities.
The IAST Advantage
- Holistic View: Combines static and dynamic analysis for a comprehensive evaluation.
- Speed: Offers faster feedback compared to separate SAST and DAST processes.
- Accuracy: Reduces false positives by analyzing vulnerabilities in their runtime context.
Potential IAST Pitfalls
- Complexity: Requires a more intricate setup.
- Overhead: The agent can sometimes affect the application’s performance.
IAST is versatile. You can utilize it during the development and testing phases for a comprehensive overview.
IAST Tools
IAST tools bridge the gap between static and dynamic testing. Some of the prominent IAST tools available are:
- Contrast Security
- Seeker by Synopsys
- Qualys
- Semgrep
- JFrog
- Code Dx
- Acunetix Ltd.
- FindBugs
- Seeker IAST
- Security AppScan
SAST vs DAST vs IAST: A Comparative Analysis
Key Similarities
All three methodologies aim to bolster application security. They identify vulnerabilities and offer insights for remediation, ensuring robust software health.
Distinctive Differences
While they share a common goal, their approaches, benefits, and limitations vary considerably. SAST focuses on source code, DAST on runtime vulnerabilities, and IAST integrates both worlds.
Comparing Scanning Tools: SAST, DAST, and IAST
Understanding the distinctions between these scanning tools is crucial for a tailored security approach. While some projects might benefit more from SAST, others might need the depth of IAST or the practical approach of DAST.
SAST and DAST Tools Combined
For comprehensive application security, integrating both SAST and DAST tools can be beneficial. This combination provides a holistic view of potential vulnerabilities, ensuring both code-level and runtime security.
Real-world Examples
SAST in action: Consider a banking app. SAST would scrutinize its code to ensure no loopholes could allow unauthorized access to account details.
DAST in action: For a shopping app, DAST would simulate transactions to ensure that real-time data transfers are secure.
IAST in action: Think of a social media app. IAST would monitor for vulnerabilities as new features are added, ensuring seamless yet secure user experiences.
Choosing the Right Approach
When it comes to application security, there isn’t a one-size-fits-all. The ideal approach is often a combination. For early development phases, SAST is indispensable. As you move into deployment, DAST and IAST become crucial, with the latter offering insights during the integration process. And for real-time attack prevention, don’t forget RASP.
However, it’s not about pitting SAST against DAST or IAST. It’s about orchestrating them in harmony to fortify your applications from every possible angle.
Conclusion
The debate on SAST vs DAST vs IAST isn’t about which is superior, but rather which is apt for your unique needs. By understanding each’s strengths and limitations and by leveraging the best SAST tools, best DAST tools, and IAST tools, you can fortify your application against threats and ensure smooth sailing.
For a comprehensive cybersecurity stance, leveraging a blend of these methodologies is essential. If you’re looking to enhance your application security, Nextdoorsec offers a deep understanding of these testing paradigms to ensure robust protection against threats.
FAQs
1. What is the difference between SAST and DAST and IAST?
SAST analyzes an application’s code without running it. DAST tests the running application externally to find vulnerabilities during its operation. IAST combines both, monitoring a running application from within to detect vulnerabilities in real-time.
2. What is IAST and SAST in DevOps?
In DevOps, SAST identifies vulnerabilities during the coding process, while IAST provides real-time feedback during the testing and staging phases, complementing the CI/CD model.
3. What is the difference between IAST and rasp?
IAST identifies vulnerabilities in a running application by analyzing its behaviors. RASP actively protects a running application by detecting and blocking threats in real-time.
4. What is the difference between IAST and Pentest?
IAST is an automated approach that continuously monitors running applications for vulnerabilities. Pentesting is a manual or semi-automated approach where ethical hackers try to exploit vulnerabilities, giving a snapshot of an application’s security posture.
5. Is SCA a part of SAST?
Not quite. While both analyze source code, SCA is specific to open-source components.






0 Comments