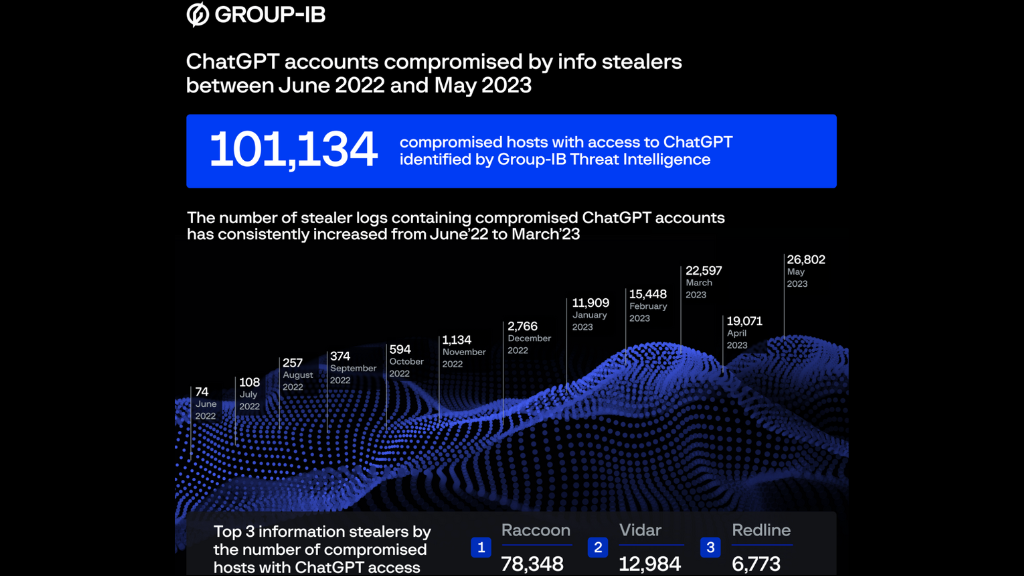
Statistics from the dark web market indicate that over the last year, spyware intended to steal data has illegally obtained over 101,000 ChatGPT account details.
Group-IB, a cyber intelligence firm, has reported the discovery of over a hundred thousand records of stolen information from ChatGPT accounts on various underground websites. Most incidents occurred in May 2023 when malicious actors posted 26,800 new ChatGPT credentials.
The Asia-Pacific area was the most frequently hit from June 2022 to May 2023, with about 41,000 hacked accounts. North America came in sixth with 4,700 hacked accounts, while Europe came in second with roughly 17,000 affected users.
Information stealers refer to malware that explicitly targets account data stored in applications such as email clients, web browsers, instant messengers, gaming services, and cryptocurrency wallets.
These types of malware are notorious for extracting credentials saved in web browsers by accessing the program’s SQLite database and exploiting the CryptProtectData function to decrypt the stored secrets.
The compromised information, including the passwords, is then collected into records and delivered back to the systems of the hackers for recovery.
The vulnerability of ChatGPT accounts, in addition to other forms of data normally aimed at, such as email addresses, credit card numbers, bitcoin wallet information, and others, emphasizes the increasing importance of AI-powered applications to consumers and organizations.
Unauthorized access to a profile could reveal secret data, insider business tactics, private chats, program codes, etc., because ChatGPT allows members to save chats.
Dmitry Shestakov from Group-IB comments, “Many enterprises are incorporating ChatGPT into their operational processes. Employees communicate informally or use the bot to improve confidential code. Given that ChatGPT’s default configuration retains all conversations, obtaining account credentials could inadvertently provide a wealth of sensitive intelligence to threat actors.”
Also Read: “Patching Security Holes: ASUS Firmware Updates Resolve Multiple Vulnerabilities in Router Models”
Concerns of this nature have prompted tech giants like Samsung to prohibit ChatGPT on work computers, even threatening termination for employees who fail to comply with this policy.
Group-IB’s data indicates a steady increase in stolen ChatGPT logs over time. The majority, nearly 80%, originate from the Raccoon stealer, followed by Vidar (13%) and Redline (7%).
If you input sensitive data into ChatGPT, it is advisable to turn off the conversation-saving feature in the platform’s settings menu or manually delete those conversations once you have finished using the tool.
However, it is essential to note that many information stealers capture screenshots of infected systems or utilize keylogging techniques. Therefore, even if you do not save conversations to your ChatGPT account, malware infection could still result in a data breach.
Unfortunately, ChatGPT previously experienced a hacking incident where users could view other users’ private information and conversation requests.
As a result, individuals working with sensitive information should not trust cloud-based services for inputting such data but should instead rely on secure, locally-built, and self-hosted tools.






0 Comments